More businesses and organisations are reliant on technology now than any time in the past. This shift to connectivity has come with an increase in use of cloud services (such as Office 365, Google Suite, Google Drive, WeTransfer, DropBox, Box, Hubspot, AWS, Azure, etc…) and with an increase in remote working.
With this connectivity and with more teams accessing organisational resources remotely cybercriminals are provided with more opportunities to launch attacks. Cybercriminals have been paying attention to this change and are constantly evolving their techniques and tactics to bypass cyber defences.
There are many types of cyber-attacks but over the last couple of years, we have seen three rise to prominence:
Ransomware
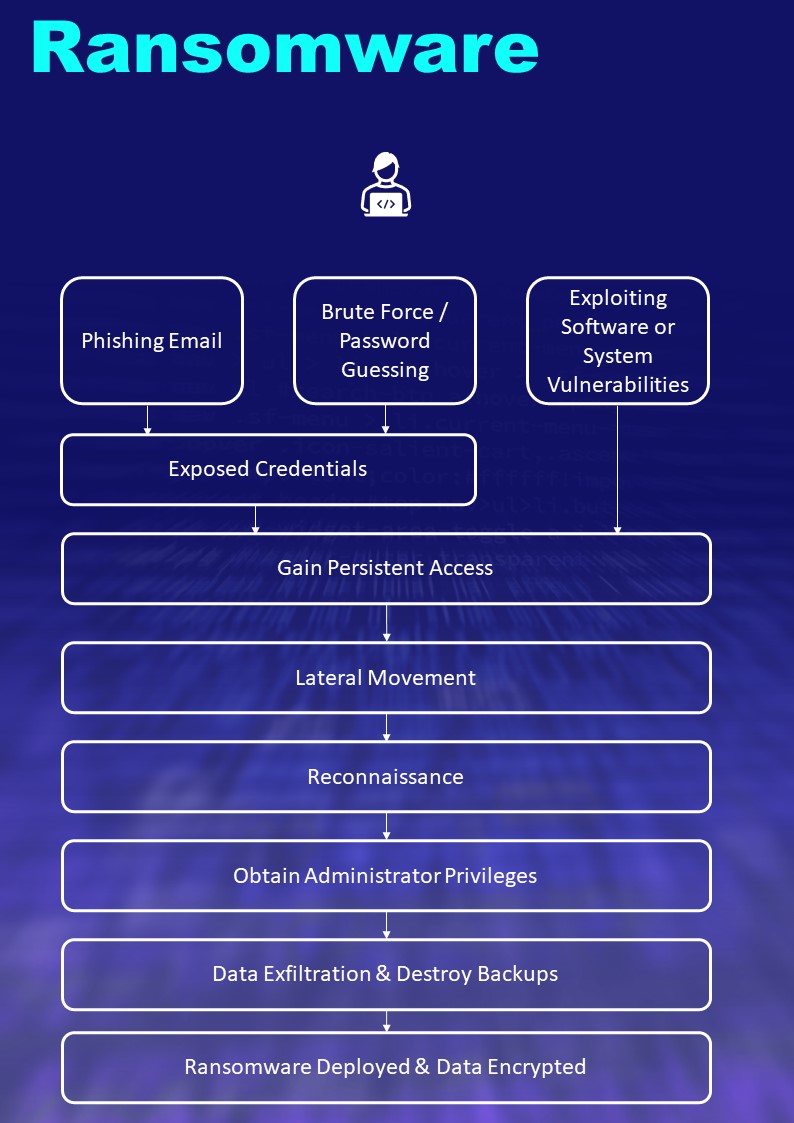
Which involves the use of malicious software to designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. The attackers then demand a ransom in exchange for decryption.
Ransomware actors often target and threaten to sell or leak exfiltrated data or authentication information if the ransom is not paid. Modern ransomware attacks use strong encryption algorithms which make decryption impossible without a key. Ransomware attacks can cause significant organisational disruption with core internal services and servers, such as email, file shares, line of business applications, CRM and ERP systems, being completely disabled for 3-14 days.
Some attacks can take longer to recover and without reliable back-ups or paying the ransom recovery can be difficult. Ransomware is developed by experienced cybercriminals who regularly adapt their techniques, tactics, and re-develop their software to evade cyber defences and cause maximum damage. The most recent evolution of attacks has seen cybercriminals steal the victim’s data prior to encryption with the threat to leak sensitive and confidential information on the internet.
Distributed Denial of Service (DDoS)
DDoS attacks as they are more commonly known, are used to flood victim’s websites or services, typically web servers or network resources. The attack is usually only temporary but can cause considerable damage and disruption, especially if they are conducted towards the victim’s customer facing websites or web services, as they can cause those systems to become overloaded and unusable for the duration of the attack.
In 2021, we saw the rise of triple extortion threats launched against ransomware victims, where attacks first compromise and encrypt a system, then threaten to leak confidential and sensitive data, then whilst the IT team and organisation are trying to recover, a third DDoS attack is launched to add further pressure on the victim to pay.
Phishing, Business Email Compromise, and Invoice Fraud
Phishing is a type of cyberattack that uses email, SMS, phone or social media to entice a victim to share personal information. In the corporate domain phishing attacks are more likely to target account names and passwords. Phishing kits are available to buy on the dark web and impersonate well-known websites. Once the victim is lured to the site they will then be prompted to enter their account name and password.
These credentials can then be re-used by attackers, potentially to access internal resources, such as Microsoft 365 email. Once the attacker has the credential and access to internal resources, they can conduct research for additional targets within the organisation they may wish to gain access to, or even try to intercept payments and invoices to direct payments to their own accounts (invoice interception and invoice fraud).
Invoice interception is commonplace, and it is not unusual for large payments (£10K-100K) to be inadvertently diverted to the accounts of the attackers.
Because of the increased risk and prevalence of cyber-attacks, in October 2021, Lindy Cameron the chief executive of the UK’s National Cyber Security Centre warned that “Ransomware presents the most immediate danger to the UK businesses and most other organisations.”
This article looks at some of the measures you can implement to protect and help prevent ransomware attacks from impacting your organisation.
This article looks at measures you can take to help protect your organisation from ransomware attacks.
Strategic Measures:
- Cyber-attacks can be extremely disruptive to organisations, with critical business systems often being offline from a few days to weeks or months. It is important to make sure cybersecurity is a board-level concern and ensure there is a dedicated budget and resources are aligned.
- Speak to IT partners and service providers that you work with and ask what their experience is with dealing with ransomware attacks. Consult with cybersecurity specialists if you feel your providers lack the necessary experience or skills.
- Create, document, and rehearse an incident response plan. Plans should be rehearsed on an annual basis and include both internal and external stakeholders, such as senior management, IT, HR, legal, finance, and service providers.
- Develop and implement a backup plan for your organisation. Implementing offline backups that are not connected to your network or devices, can help reduce the risk of a ransomware attack leading to your backups being deleted. The recovery process for backups should be regularly tested.
Technical Measures
- Build a reliable asset management process to identify what needs to be protected and who is responsible for them. This should include the identification of critical assets and determine the impact to these if affected by a ransomware attack. Ransomware attack groups will usually disable critical business systems including telephony, email communications, payment services, file servers, business applications, CRM, and ERP systems.
- Use strong, complex passwords and do not reuse passwords across accounts. Reusing passwords across websites, systems and accounts makes it extremely easy for hackers to gain access to other accounts that you use the same credentials for. Organisations should require the use of multi-factor authentication (MFA) across the organisation. MFA can stop the use of stolen credentials from being easily reused.
- Ensure known vulnerabilities of devices and infrastructure are regularly patched, especially with critical vulnerabilities and with security-enforcing devices on the network, such as firewalls and virtual private networks (VPNs).
- Ransomware attacks are usually stealthy and able to evade detection from basic antivirus and anti-malware products. So, consider implementing behavioural-anomaly-based detection technologies such as Endpoint Detection and Response (EDR), or Extended Detection and Response (XDR).
- Enforce the principle of least privilege. Administrator accounts should have the minimum permission they need to do their tasks. Ensure there are unique and distinct administrative accounts for each set of administrative tasks. Create non-privileged accounts for privileged users and ensure they use the non-privileged accounts for all non-privileged access (e.g., web browsing, email access).
Next Steps
It is advisable to review the websites of the UK National Cyber Security Centre and the US Critical Infrastructure Security Agency. Both organisations, regularly post best practice and guidelines for protecting against ransomware attacks. You can view these pages here:
https://www.ncsc.gov.uk/guidance/mitigating-malware-and-ransomware-attacks
https://www.cisa.gov/uscert/ncas/alerts/aa20-245a
If you want help or assistance implementing any of the measures detailed above, you can contact us at 020 7193 4905 or [email protected]
A PDF copy of this article can be downloaded here.
How We Can Help
If you have a cybersecurity incident, believe you are under attack or have been compromised, then call us immediately for assistance on 020 7193 4905 or email us as incident [at] first-response.co.uk
Managed cybersecurity services can help prevent ransomware attacks by detecting and stopping attacks at the initial stage of the attack cycle, our managed detection & response includes an extended detection & response platform with full 24/7 coverage by our security operation centre (SOC), our managed cybersecurity services are detailed here.
Not every attack can be prevented, therefore it is important to have a plan in place should the worst happen. Details on our cyber incident response plans and readiness is available here.
Other Articles of Interest