Recently, a friend received an email message addressed to his private company’s email address, telling him that a number of his mail messages had been quarantined.
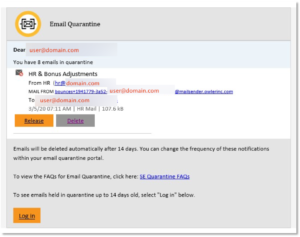
The relevant part of the message is shown here (with recipient user and domain names redacted).
This is an excellent example of ‘spearphishing’ – that is, phishing which is very narrowly directed towards a specific individual target or group of targets. The interface and look and feel appeared somewhat familiar, so my friend clicked the link to log in. This brought him to the sign-in page for Microsoft’s Office 365 service. Here, his Spidey sense kicked in – he doesn’t use Office 365 for his private company business – and he moved swiftly in the general direction of away.
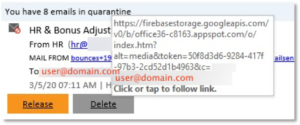
Here’s what the link showed him when he hovered over it:
He commented, “Clever stuff! …And no, I didn’t give them any credentials despite not having had my coffee yet this morning. But I might try logging in with a wrong password and then trace the subsequent failed attempts on my actual domain.”
Morals: First, take the time to hover over links in messages like this and see if they appear to be genuine. Beware of links such as https://login.microsoft.com.xyz.ru?alt=media&token=46D30200F76B83582AED. Second, don’t respond to these things before you’re fully awake. If, like me and many others, your first instinct in the morning is to go through your mail, and dispose of any outstanding issues, and you feel rushed or not yet fully awake, stop and wait until you are sure you know what you’re doing.
Facebook ads
If you own a Facebook page (as opposed to a Facebook account), you may well have received Facebook messages, or even email messages, letting you know that you can be paid large amounts of money (typically over £1000/week) if you allow the sender to post ads on your page.
This may also occur if you run a WordPress or other non-commercial blog site.
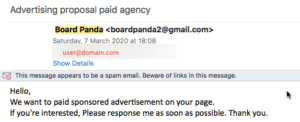
Sometimes they appear to be from a legitimate site (until you notice the lack of a subject line and the gmail address – not to mention the lack of detail):
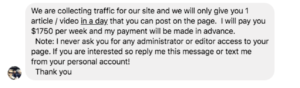
And sometimes they get it dramatically and amusingly wrong:
The two above were to my non-commercial blog contact details.
So what’s the scam? As I understand it, the rewards for the scammer are not directly financial. Once you accept one of these over-generous offers, this is what happens (copied and pasted from another one of these scam mails, which generously explained the process in detail):
- Publishing: 1 content per day
- Amount: $600 per week
- How to join website? You will recieve [sic] an invitation mail for sign up
- Terms and conditions: facebook verification to join website, Add page to publish contents [THIS IS THE CATCH!]
- Payment terms: PayPal, Western Union, Payoneer.
- Publishing tool: Assign any admin in publishing tool who can publish our contents every day.
- Duration: 4 weeks
Note that although this was addressed to the contact address for my WordPress blog, the instructions reference Facebook – and this is where the con moves into top gear. Once step 3 is completed, and you sign up, you are invited to complete the “Facebook verification”. This is of course a fake page, specifically created for the purpose of harvesting passwords. Once you have entered your password, it is immediately changed, and you are then locked out of Facebook. Not only that, but if you are one of those people who reuses passwords for Facebook, Outlook, and other logins (and if you are reading this, you aren’t one of them, are you?) – your password is added to a database that will circulate on the dark Web.
So, as always – if it sounds too good to be true, it probably is. This is a very simple scam, but it is obviously effective enough to be worth carrying out. Don’t fall for the promise of easy money – it could cost you more than you realise.