One of the most virulent carriers of malware is on the loose – again
The popular image of computer hackers is one of pimply geeky nerds sitting in their parents’ basements, guzzling quantities of fizzy drinks and pizza while endlessly typing in passwords in order to access forbidden systems.
The reality is much more sinister. Crime is a serious business, and those pursuing a career in cybercrime may well be part of an enterprise that is more efficiently run and more profitable than the organisations that form their prey.
This is largely due to the evolution of ever more sophisticated tools enabling the threat actors to launch their attacks. One such, which has recently attracted a lot of attention through recent activity is Emotet, which in itself is not destructive malware, but is a sophisticated method of delivering ransomware and other crippling payloads to their targets.
Although it has retained the same name over the years since its first appearance in 2014, Emotet has evolved over time in its methods of operation and the way it infiltrates its targets. Starting as a method of delivering banking Trojans, it is now capable of delivering double knockout blows simultaneously, such as the TrickBot and Ryuk harvester and ransomware malware, while evading protection software. It’s modular, and thereby easily customisable to perform specific tasks.
These tasks multiply at a terrifying rate – one security software provider counted a total of over 4,900 unique payloads delivered by Emotet in the last two weeks of January 2019. The number continues to grow and Emotet continues to be a major threat.
Who uses Emotet?
As mentioned earlier, the deployers of Emotet are not the Hollywood geeks of fiction. Indeed, like their victims, they are consumers of cloud-based services. There are organisations that maintain and develop new versions of Emotet, making it available to those willing to pay for it.
Malware as a Service (MaaS) is a relatively new development, which opens the doors of crime to anyone with the money to pay for access. No longer does the criminal organisation require inhouse technical expertise, or even high-speed Internet connections, since these are provided by the MaaS providers and come as part of the package.
Clearly this multiplies the number of potential attacks considerably, from a wide variety of sources. Targets, however, are typically those from which the richest pickings can be expected: the USA, Canada, the UK, northern Europe, etc. with other cases reported from China and Brazil.
How does a system get infected?
Sadly, the most common method of infection is still through human beings – the inability to distinguish fake from real.
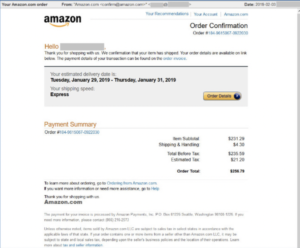
Figure 1: Emotet phishing email – source, SophosLabs
A victim may be informed that his/her Apple/iCloud account has been suspended, or that a credit card transaction has been refused. Clicking on the link to put things right again will open a site from which the Emotet will move into the victim’s machine.
Macro viruses embedded in Word documents are another common vector for Emotet infection, then spreading rapidly from the originally infected computer to the whole system.
Millions of phishing email messages sent out will guarantee statistically that someone somewhere will click on the link and open the way to a financial bonanza for the attacker.
What to do?
As with all such attacks, the best cure is prevention – as far as possible.
- Create spam and phishing awareness throughout the organisation. Hold training sessions (can be achieved through Web participation) and repeat them at regular intervals.
- Create and enforce a policy which prohibits the use of macros.
- The organisation’s security policy should prohibit the running of executable files in temporary folders.
- Set up a multi-faceted defence against Emotet, which may involve network appliances, endpoint security software and other security solutions.
- First Response consultants can assist you in strengthening your enterprise against Emotet and similar attacks, not only on the technological side, but also in the development of corporate policies which work to keep the attackers from gaining access to your systems.
And if you have been infected:
- As soon as possible, change the user credentials (name and password) of any users whose systems are known to be infected.
- Call in the experts. First Response have seen Emotet infections before, and our security consultants know the best practices to recover from malware attacks, whether ransomware or data theft. We can provide an expert rapid response to minimise the fallout from malware infections and also help you guard against future attacks.
