Passwords are a perennial problem. In a perfect world, we wouldn’t need passwords (or padlocks, or police officers, or burglar alarms). We could trust the world to mind its own business, and not interfere in ours. But as we are all too aware, our homes and businesses and our computers seem to present tempting targets to those we would sooner keep outside.
Hence passwords. When I first started to use computers at university, we used a time-sharing system, with ancient Teletype terminals. We were each given a 4-digit user ID, and told to choose a password. Time on the machine was strictly limited, and I quickly used up my ration. So… my number was 5422, so I guessed there was a 5423, and, being of a creative turn of mind, guessed that the password for that account might be 3245 (see what I did there?). My guess was proved correct, and I finished the project.
Of course, now we all need many passwords, and they are more complex than the four digits I was able to guess so easily. How to remember them all, though?
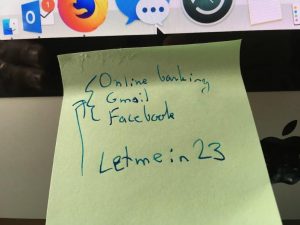
The security nightmare – the yellow sticky note with all the important passwords, carefully stuck to the monitor or under the keyboard where it can’t be missed.
The answer, of course, is to use one of the many excellent password vaults on the market, which only require you to memorise a single password to unlock an encrypted database of all your passwords (and often other things such as credit cards and so on). One key opens many doors.
Somewhat similar to the master password concept, some major Internet platforms have offered themselves as ’master keys’ which will authenticate users on less well-known sites.
Your Google account can be used to sign in on many sites, and so can your Facebook or Twitter credentials. In effect, by accepting this model, we have assigned trust to these major entities, in the same way that we assign trust to our neighbours when we go away for our holidays and leave the key with them.
But what happens when they leave the key in the local bar for anyone to pick up? Basically, this is what happened with Facebook earlier this month (September 2018). Over 50 million, and some reports say up to 90 million accounts, have potentially been accessed through a flaw in the code that runs the site.
The access tokens that Facebook provided for Facebook users to run other applications and access other sites and services may well have been stolen.
No-one outside Facebook, at the time of writing, knows how many third-party applications may have been compromised, or even how long this vulnerability has been exploited by malicious threat actors. It is reported that the vulnerable code has been in place since July 2017.
What does this mean for you?
If you’re running a site which provides services to users requiring a login, you should consider avoiding the use of access tokens provided by these major platforms. It may even be the case that the use of these access tokens to protect personal information is considered an insufficient mechanism under GDPR by regulators.
Partnering with a major internet vendor to provide pass-through-authentication to your site may seem like an inexpensive option to solve a tricky problem, but time and again, we see that it’s often the bigger and more complex platforms that fail most spectacularly. Taking ownership of your security boundary needn’t be expensive and your first port of call should be ensuring that your passwords are not only robust and secure, but under your sole control.
Contact First Response:
or email us at:
[email protected]
