Record what we find – intelligence, evidence and unused material
It has been a few months since my last post on open source investigations and I want to pick up where I left off. The question now is ‘what do we do with all this open source information when we have found it?’ I believe in simplicity and have been using the following methodology in my open source investigation work since 2009. It works, allowing the, ‘what do we do with the information?’ question to be answered. This methodology has withstood detailed scrutiny by several defence teams in high profile criminal cases here in the UK over the last few years. It is also the core part of the open source training that we deliver.
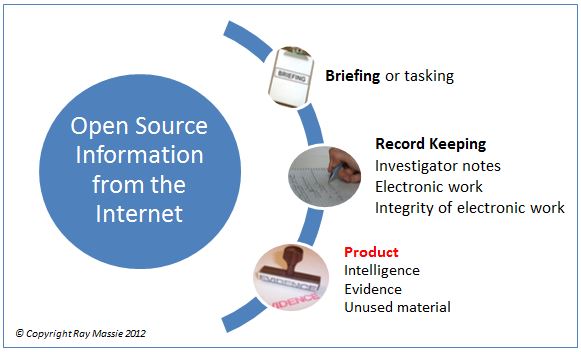
The methodology has the following parts to it:
Briefing or tasking
A simple enough concept but I put a pro-active emphasis on this. Asking the correct questions at this stage can save hours of fruitless research later. Part of this pro-active approach is adding to the questions the researcher asks, especially: ‘is this known or can it be ascertained?’ The key is to have a set of questions ready for the moment you are tasked with carrying out open source.
Investigator Notes
There are two parts to this, a contemporaneous record of the work carried out by the investigator and the electronic/digital work itself. Giving the electronic work integrity by using a hashing algorithm, as practised in computer forensics is also a fundamental part of the record keeping process.
Product
By following a structured methodology it does not matter what the end product turns out to be. It can be produced and graded as intelligence or produced as evidence. What is left can be scheduled and made available for 3rd party inspection whether as unused material in a criminal case or to satisfy other regulatory obligations.
This methodology can be easily incorporated into your working practices and is not onerous to follow. The use of a master and working copy of the electronic work, together with the checksum and correct ‘chain of custody’ handling & storage of the master copy, has helped this methodology withstand close scrutiny by criminal defence teams.
Having delivered presentations on open source investigation to a variety of audiences over the years I have sometimes been confronted with ‘horror stories’ about internet based material being used in criminal trials or that a prosecutor will simply not allow it to be presented. Generally the ‘horror stories’ end with evidence being excluded.
Having looked at a number of these cases, I have found that it is usually the way in which the material is collected, handled or presented that is the cause of the problem – it is rarely the material itself.
Like many aspects of investigations, it is the lack of documentation surrounding how material is obtained that gets scrutinised and found wanting. The methodology allows investigators to demonstrate a professional, transparent process around how any internet based material is collected, handled and presented. It will also assist investigators in meeting any 3rd party obligations around retention and disclosure.
By Ray Massie – Operations Director, First Response
Click here to read how we helped a multi-national development company with a digital forensic investigation.