What is Ransomware
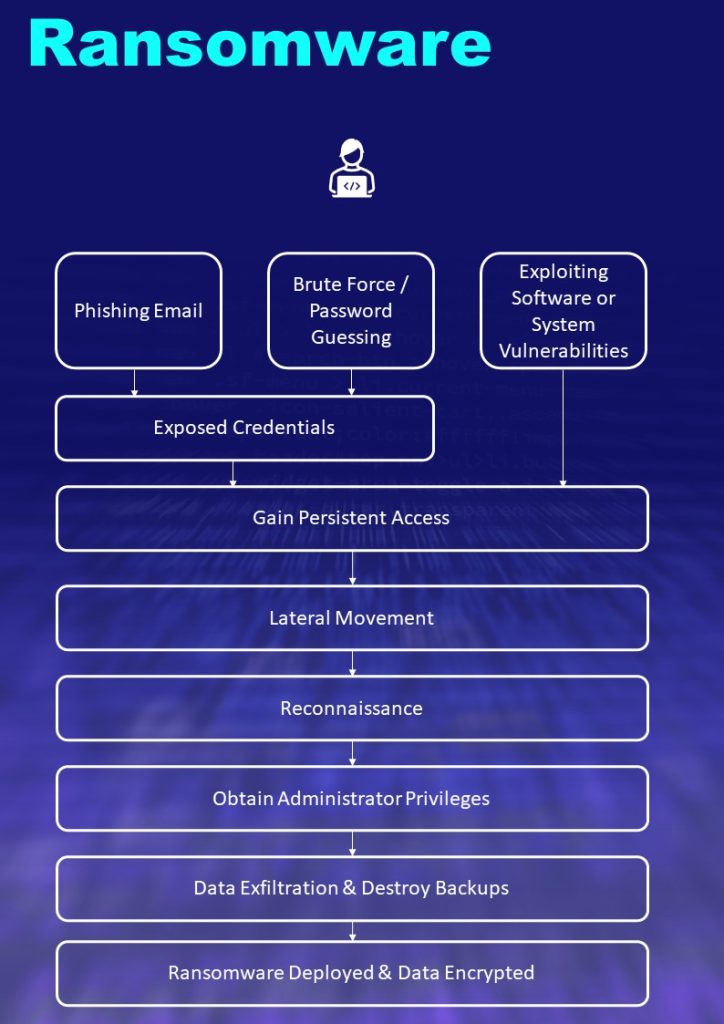
Ransomware is a specific type of malicious software which is used in ransomware attacks. Ransomware attacks are often caused by organised cybercriminal networks (the FBI is currently tracking over 100 active ransomware groups).
First Response provides cyber incident response services and incident response for ransomware attacks, both are detailed here. Details on our cyber incident response plan and incident response preparations are here.
Successful ransomware attacks can:
- encrypt devices, servers, desktop, and laptop computers
- cause devices to become locked or unusable
Ransomware attack groups are highly-organised and have consistently developed their tactics and techniques, to evade detection from cyber defences and to ensure maximum success of ransom payments. They will usually target victims with the intent to:
- steal, delete or encrypt data
- take control of your devices to attack other organisations
- obtaining credentials to gain allow access to your organisation’s systems or services that you use
- destroy, or encrypt your organisations backup systems
- sell or publish your stolen data on the internet
- launch distributed denial of service (DDoS) attacks after they have completed the last phase of the ransomware attack
Once your computers and servers are encrypted it is often impossible to gain access to those systems without the decryption key from the attackers, or without good quality backups.
Backup policy differs across organisations and some organisation may find that even with backups they cannot recover their data. Often this is because the backups are too old to recover from, it would take too long to recover from the backups, the attackers disabled/deleted the backups, or because the backups have been compromised during the attack and are unusable.
Once the attackers have completed their attack they will usually request that the victim contacts them via the darkweb, they will then try to begin negotiations with you for the decryption key. It is important to note that even after paying the ransom there is no guarantee the decryption key will work, or that you will be able to recover your data. This is why it is important for organisations to implement a robust security strategy to deal with the threat of ransomware.
In this article:
- What is Ransomware
- Types of Organisations Ransomware Attack Groups Target
- Types of Services and Systems Ransomware Attacks Target
- Double Extortion
- When You Ned an Incident Response team
- Common Problems When Handling Ransomware Attacks
- The Core Incident Response Team
- Detection & Analysis
- Regulatory Implications
- Guidelines
Types of Organisations Ransomware Attacks Groups Target
All organisations are potential targets for ransomware attack groups. Some groups have stated publicly that they will not target specific types of organisations such as non-profits, schools, or hospitals. Unfortunately, these types of organisations may still be a target for other attack groups. This is evident on the attack on the Irish health service in 2021:
Types of Services and Systems Ransomware Attacks Target
- Telephony/VOIP
- Cloud applications and cloud services
- File servers and file shares
- Line of Business applications
- ERP and CRM systems
- Other core IT infrastructure such as Domain Controllers and Active Directory
Double Extortion
Ransomware attack groups are constantly changing their approaches and tactics to ensure maximum damage to organisations. Over the last few years there has been an increase in the trend for these groups to steal confidential information and data from an organisation prior to them encrypting systems and services. They then threaten to leak this information if the ransom isn’t paid.
When You Need an Incident Response Team
Attackers will move across a computer network conducting reconnaissance and gathering intelligence as they move. The initial phases of an attack may last a few weeks or days, but the last phase of the attack can happen very quickly. Once the attacker has disabled an organisations defenses and the encryption process has started, an organisations IT system could be encrypted in a matter of hours.
This can make it very difficult for IT and security teams to respond as they are often under extreme pressure from the executive team to bring systems back online.
If the IT or security team is inexperienced when dealing with ransomware incidents or if there are complications during the recovery process, it is usually best to call in an experienced incident response team. This is to ensure the organisations IT systems are restored effectively and efficiently.
In some scenarios IT teams have inadvertently restored from backups too soon which has then led to the backups being compromised, it is also possible that systems are brought back online whist the attacker is still inside the network, or that the original root that the attacker took to compromise the system hasn’t been remediated; meaning they could return at a later date.
It may also be the case that your organisation doesn’t have the requisite technology in place to conduct a forensic investigation or to thoroughly complete the remediation process.
Common Problems when Responding to Ransomware attacks
With ransomware incidents, we often see that companies don’t communicate well, this is not surprising as for IT and executives it may be the first time they’ve had to handle a situation of this nature. Clear, straightforward communication is essential when dealing with any incident, but with a ransomware it is especially important.
Another common misconception we see fairly regularly, is the expectation that a cyber incident or ransomware attack is solely an IT problem and that “We just need the IT team to deal with it.” Because of the potential financial, operational, legal and reputational ramifications, it is important that the composition of the core Incident Response Team focusses on senior management to ensure that the decision-making process remains swift and that decisions are not deferred or delayed by those lacking the appropriate authority.
Representative Composition of the Core Incident Response Team:
- Board Representative or CEO/CFO
- Director for Regional Operations
- Technical Services Director
- Head of Legal & Compliance
- Head of Internal Audit
- Head of IT & Cybersecurity
- Head of Human Resources
Detection & Analysis
Once an incident has been detected it should be assessed and categorised according to the organisations incident response framework.
Organisations without a written and documented cybersecurity incident response plan will most likely lack a process for reporting, assessing and triaging potential incidents. However, if you decide to engage with an external IR team, there is specific data and information around the incident that should be captured, including (but not limited to):
- What type of attack is it (validate whether it is actually ransomwware and not phishing or other malware)
- Which systems are affected (i.e. which applications, networks, servers and services are affected)
- What are the indicators of compromise (files/hashes, processes, network connections)
- What data is affected (e.g., file types, department or group, affected software)
- How critical is the data
- How sensitive is the data
- What is the regulatory status of the data (i.e. PCI, PII, PHI)
Source: adapted from https://github.com/counteractive/incident-response-plan-template/blob/master/playbooks/playbook-ransomware.md
Network diagrams and supporting information should be prepared, detailing:
- Internet gateways
- IP address ranges and any separate VLANs
- remote access
- key systems (file servers, platforms, domain controllers, webservers)
- physical locations of servers
You should also document all security devices and software which could be useful during incident response.
Source: https://www.ncsc.gov.uk/collection/incident-management/technical-response-capabilities
Regulatory Implications
If you’ve discovered a personal data breach likely to result in a risk to the rights and freedoms of individuals, you must report it within 72 hours under the UK GDPR to the Information Commissioner’s Office (ICO). You may also need to report incidents to stakeholders, such as regulators, insurers, customers or partners.
Guidelines
If your team lacks the necessary experience in responding to ransomware you should seek guidance from outside specialists.
First Response has experience working on over 200 cyber incidents, including large and small ransomware attacks, across public and private sector organisations.
How We Can Help
If you have a cybersecurity incident, believe you are under attack or have been compromised, then call us immediately for assistance on 020 7193 4905 or email us as incident [at] first-response.co.uk
More information on the cyber incident response services we provide is available here.
We also provide a pro-active managed detection and response service for Microsoft Defender, details are available here.